Subtotal $0.00
Cyber Essentials Plus is the UK government's advanced cyber security certification, but it's much more than a compliance badge. It's a verified, hands-on technical audit performed by an independent expert. Think of it less like a theoretical exam and more like a rigorous 'MOT' for your company's digital defences, where your systems are actively tested against the kinds of attack methods used in the real world.
Proving Your Security Beyond a Checklist
In an era where data breaches are a persistent business risk, simply claiming your organisation is secure is no longer enough. Customers, partners, and regulators require tangible proof. This is where Cyber Essentials Plus delivers real-world value, moving your business from simply declaring its security posture to actively demonstrating it.
It serves as powerful, independent verification that your foundational cyber defences are not just in place but are configured correctly and can withstand realistic attack simulations.
The Verification Difference
Unlike the standard Cyber Essentials scheme, which is based on a self-assessment questionnaire, the Plus level introduces the critical element of independent validation. This is what gives the certification its authority and credibility. The process isn’t about ticking boxes on a form; it’s about a qualified assessor methodically probing and testing your security controls to see if they hold up under pressure.
This shift from self-declaration to third-party verification transforms the certification from a baseline compliance exercise into a genuine mark of security assurance. It builds tangible trust with everyone from clients to insurers.
What Does the Audit Involve?
The Cyber Essentials Plus audit is a practical, deep-dive assessment. A certified assessor performs hands-on testing of your core technical controls to ensure they are robust enough to fend off common cyber threats like malware and unauthorised access.
This isn't a superficial check. The audit covers key areas of your IT environment, including:
- Firewalls
- Secure configurations
- User access controls
- Malware protection
The goal is to ensure your security isn't just theoretical but is practical and effective in a real-world context. You can find more detail on the latest certification requirements from official sources like cybercrowd.co.uk.
Achieving this standard sends a strong signal that you've invested in a resilient security posture. It demonstrates a commitment that goes beyond the bare minimum, showing that your organisation has put its defences under impartial scrutiny. For many businesses, successfully navigating this process is where structured IT support becomes indispensable, ensuring systems are correctly configured and ready to pass the audit without costly delays or failures.
Cyber Essentials vs Plus: The Key Differences Explained
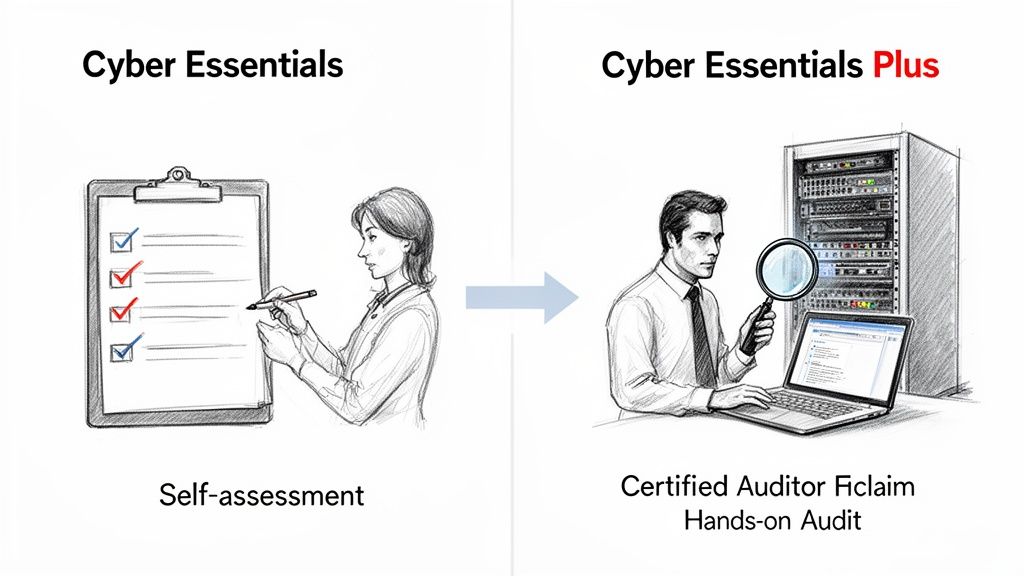
When exploring Cyber Essentials, it's easy to get confused by the two tiers. The crucial distinction isn't about the security controls themselves—both certifications are built on the exact same five foundational security pillars.
The real difference comes down to one simple but powerful concept: verification. How do you prove you are actually implementing the controls you claim to have?
Think of it this way: Cyber Essentials (Basic) is like declaring you've revised for an exam. You’ve studied the material and you feel confident you know the answers. Cyber Essentials Plus is the supervised exam itself, where an independent expert comes in to test that knowledge under real-world conditions.
From Self-Declaration to Audited Reality
The standard Cyber Essentials Basic certification is a trust-based exercise. Your organisation completes a detailed self-assessment questionnaire (SAQ), confirming that you have implemented the required security measures. It's an excellent first step for establishing a security baseline, but its authority is limited because it is self-declared.
Cyber Essentials Plus changes the dynamic completely. It takes the answers from your questionnaire and rigorously tests them with a hands-on, technical audit from an independent, accredited assessor. It’s no longer about saying your defences are in place; it's about proving they actually work.
An auditor doesn't just ask if your doors are locked; they actively try to open them. This independent verification is what gives Cyber Essentials Plus its weight and makes it the gold standard for proving your resilience.
What Does the Hands-On Audit Actually Involve?
The 'Plus' audit is far more than a paperwork review. The auditor runs a series of practical tests designed to mimic the kinds of attacks a business would face from a real-world threat actor.
This typically includes:
- External Vulnerability Scan: The auditor scans your internet-facing systems—like your website and email servers—for any known security holes that an attacker could exploit from anywhere in the world.
- Internal Patch Audit: They then run a scan on a sample of your internal devices (laptops, servers) to ensure all your software and operating systems are up-to-date and patched against known threats.
- Malware Protection Testing: To test your defences, the assessor will try to deliver benign files that mimic malware through your email and web browser. The goal is to see if your security software correctly identifies and blocks them.
- Access Control Confirmation: The audit also verifies that user accounts have appropriate permissions and that powerful administrative privileges are properly locked down and controlled.
This impartial testing provides a level of assurance that a self-assessment simply cannot match. It confirms that your security controls aren't just policies on a page—they are properly configured, active, and effective.
Cyber Essentials vs Cyber Essentials Plus At A Glance
To make the distinction crystal clear, here’s a quick side-by-side comparison.
| Aspect | Cyber Essentials (Basic) | Cyber Essentials Plus |
|---|---|---|
| Verification Method | Self-Assessment Questionnaire (SAQ) | Hands-on Technical Audit by an external assessor |
| Scope of Testing | Based on answers provided in the SAQ | External scans, internal device checks, malware tests |
| Assurance Level | Foundational; demonstrates intent | High; proves effective implementation |
| Typical Use Case | Baseline security for SMEs; a great starting point | Supply chain requirements; public sector contracts |
As you can see, the jump to Plus is significant. It moves you from a position of saying you're secure to proving you're secure.
For organisations serious about winning public sector contracts, securing their place in a corporate supply chain, or simply wanting undeniable proof of their security posture, pursuing Plus isn't just a good idea—it's a strategic necessity. It demands a well-prepared IT environment, where expert guidance can often be the deciding factor in passing the audit and demonstrating that your defences are truly business-ready.
Putting The Five Technical Controls to The Test
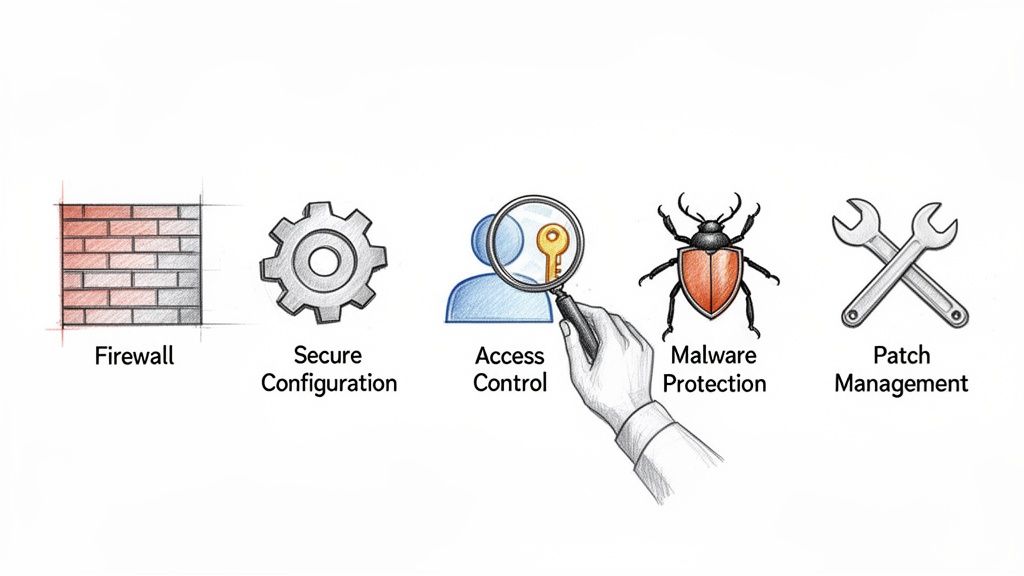
The Cyber Essentials Plus audit is where theory meets reality. It takes your security declarations and puts them under a microscope, with a certified professional actively trying to find the cracks. An auditor doesn’t just read your policies; they simulate genuine attack methods to see if your defences actually stand up to pressure.
This rigorous, hands-on verification is what gives the certification its true weight. While the five technical controls are the same as the basic scheme, the assessment is a completely different challenge. Let’s break down each control and see exactly how an auditor puts it to the test in a real-world IT environment.
1. Boundary Firewalls and Internet Gateways
Think of your firewall as the digital front door to your business, controlling all the traffic that comes and goes. During the Plus audit, an assessor doesn't just check that you have a firewall; they perform an external vulnerability scan to actively probe it from the outside, mimicking exactly what an attacker would do.
They hunt for any open "ports" that have no business reason to be accessible to the public internet. A port is like a specific door into your network; if one is left unlocked by mistake, it’s an open invitation for an intruder. A common reason for failure is a server that was set up for temporary access and never properly secured afterwards, leaving a back door wide open for exploitation.
2. Secure Configuration
This control is about ensuring your devices and software are set up for maximum security, not just out-of-the-box convenience. Auditors check that you've changed default admin passwords, removed unnecessary programs, and disabled auto-run features that malware loves to exploit.
The test involves both automated scanning and a manual review. The assessor will inspect a sample of your workstations and servers to confirm their setup. For example, they’ll look for:
- Default Credentials: Have you changed the default "admin/password" on new routers, printers, or applications? This is one of the most common and easily fixed vulnerabilities.
- Unnecessary Software: Is old, unsupported software lurking on your machines? The audit flags applications that no longer receive security updates, making them a prime target.
- User Privileges: The assessor will confirm that standard users do not have administrative rights on their machines. This simple step massively limits the damage malware can do if an account is compromised.
A secure configuration isn't a "set it and forget it" task. It requires a solid baseline that is applied to every new device and regularly reviewed—a core principle of a strong security posture.
3. User Access Control
Knowing who can access your data is fundamental to protecting it. This control is built on the principle of "least privilege," meaning people should only have access to the information and tools they absolutely need to do their jobs. The audit pays very close attention to administrative accounts—the ones that hold the keys to the kingdom.
An assessor will review your user account lists to ensure access levels are appropriate. They'll check that accounts for former employees have been disabled promptly and confirm that powerful admin privileges are tightly controlled. A frequent failure point is having far too many users with "domain admin" rights, which creates a huge risk if just one of those accounts is compromised.
4. Malware Protection
This control is about your active defence against malicious software. The Plus audit tests this in a very direct, practical way. The assessor will try to introduce harmless test files that are designed to look like malware onto a sample of your computers, using two main methods:
- Email: They will send an email containing a benign file that your antivirus software should immediately detect and block (like an .exe file disguised as an invoice).
- Web Browser: They will ask a user to visit a specific webpage that hosts a similar benign test file, checking to see if the endpoint protection stops the download.
If either of these files can be downloaded and opened, it’s an automatic fail. This practical test confirms that your anti-malware solution is not only installed but also running, up-to-date, and configured properly to block threats in real time. It reveals gaps—like a misconfigured email filter or out-of-date software—that a simple policy document would never catch. Understanding how your environment reacts is a critical part of any thorough Azure security assessment or similar infrastructure review.
5. Patch Management
Keeping your software and operating systems up to date is one of the single most effective things you can do for your security. Attackers constantly exploit known weaknesses in old software. The Cyber Essentials Plus audit ensures your patching process is actually working.
To do this, an auditor runs an authenticated internal vulnerability scan on a sample of your devices. This means they log in with credentials to get a deep look at every piece of software installed, comparing the version numbers against a global database of known vulnerabilities.
Any critical or high-risk vulnerabilities found on software that has had a patch available for more than 14 days will result in a failure. This strict deadline forces organisations to maintain a disciplined and timely approach to updates, closing security holes before attackers can exploit them.
The Strategic Business Benefits of Certification
Achieving Cyber Essentials Plus is much more than a technical exercise; it's a strategic business decision that unlocks significant commercial advantages. While strengthening your defences is the primary goal, the certification itself sends a powerful signal to the market, turning your security investment into tangible gains in reputation, resilience, and growth.
Viewing the certification as a mere compliance checkbox means missing the bigger picture. It's a genuine competitive differentiator—a clear, government-backed statement that you take data security seriously. This resonates deeply with clients, partners, and even insurers, shifting the conversation from "Can we trust you?" to "We've proven you can."
Unlocking Public Sector and Enterprise Contracts
For many businesses, Cyber Essentials Plus is the key that opens doors to major new contracts. It is now a mandatory requirement for bidding on a huge range of UK government and public sector projects, especially those involving sensitive or personal information. Without it, you are often not even in the running.
This trend is increasingly mirrored in the private sector. Large enterprises recognise that their own security is only as strong as the weakest link in their supply chain. As a result, they are more frequently demanding Cyber Essentials Plus from their suppliers to mitigate risk. It is fast becoming a non-negotiable ticket to entry for lucrative enterprise accounts.
Cyber Essentials Plus isn't just a security badge; it's a commercial passport. It proves your organisation meets a recognised standard of cyber hygiene, instantly elevating your credibility in high-value procurement processes.
Building Unbreakable Supply Chain Trust
In modern business, trust is paramount, and nothing shatters it faster than a security breach. Holding a Cyber Essentials Plus certificate provides your partners with verifiable proof that you are a secure link in their supply chain. This saves everyone time, reduces friction during onboarding, and helps build deeper, more resilient business relationships.
The impact is significant. A recent analysis found that 75% of users feel more confident working with certified partners, and a staggering 59% save valuable time on security checks. Why? Because the certification replaces endless security questionnaires with a single, trusted credential. For instance, when wealth management firm St. James’s Place mandated the certification for its 2,800 partner firms, they saw an 80% drop in security incidents. That's a powerful return on investment. You can explore the full findings on Computer Weekly.
Reducing Insurance Premiums and Demonstrating Due Diligence
The cyber insurance market is becoming more stringent. Premiums are rising, and providers are demanding more evidence of good security practices before offering coverage. Holding a Cyber Essentials Plus certification can directly influence your policy. Insurers see it as concrete evidence that you’ve addressed the most common risks, which often leads to better terms and lower premiums.
Certified firms don't just see fewer insurance claims; they also enjoy savings of 22-32% on due diligence costs. It acts as powerful proof that you’ve taken reasonable, proactive steps to protect your business and your clients' data. This strengthens your position when negotiating with insurers and solidifies your defensive posture if an incident ever occurs. Turning these security controls into a measurable business asset is where expert guidance is invaluable, ensuring your technical efforts align perfectly with your commercial goals.
Your Roadmap to Achieving Cyber Essentials Plus
Embarking on the Cyber Essentials Plus journey can seem daunting, but it becomes manageable when broken down into a clear, structured plan. This roadmap breaks the entire process into logical stages, guiding you from initial preparation right through to certification. The goal is to demystify the process and make it structured and achievable.
Preparation is everything. We've seen businesses rush into an audit without having their house in order, which almost always leads to failure, stress, and unexpected costs. A methodical approach, on the other hand, ensures your technical controls are perfectly aligned with the requirements, making the audit itself a smoother experience and boosting your chances of a first-time pass.
Ultimately, this isn't just a technical exercise; it's a strategic initiative that delivers real business value.
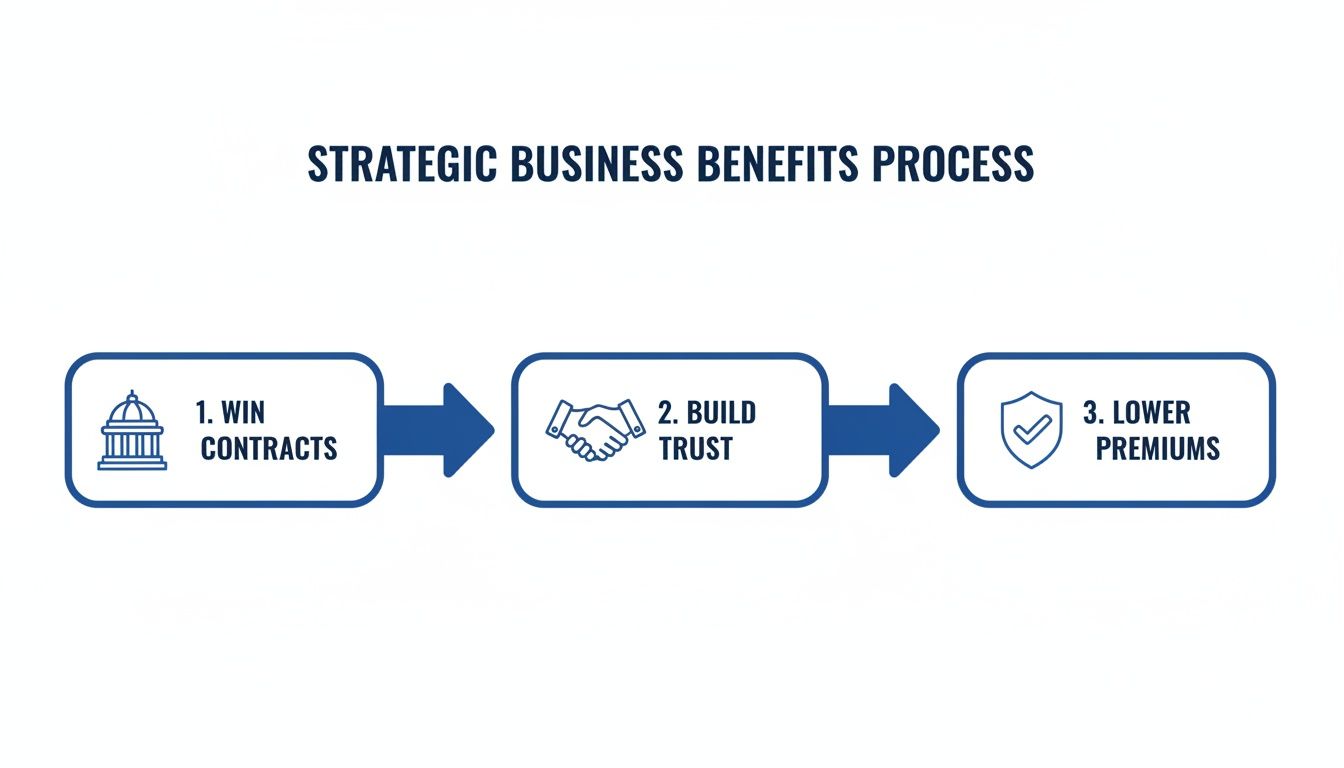
As you can see, certification directly feeds into winning new contracts, builds undeniable trust with clients and partners, and can even help lower operational costs like your insurance premiums.
Step 1: Scoping Your Environment
First, you must define the scope of your assessment. This means identifying every device and system that needs to be included in the audit. This includes all user endpoints (laptops and desktops), mobile phones, servers, and any cloud services that handle your organisation's data.
Getting the scope right is non-negotiable. Missing a device can lead to an automatic failure during the audit. This step requires a thorough inventory of your entire IT estate to ensure nothing is overlooked.
Step 2: Conducting a Gap Analysis
With your scope defined, the next step is a gap analysis. This is essentially a pre-audit health check where you measure your current security setup against the five core technical controls of Cyber Essentials Plus. The goal is to identify any weak spots or non-compliant areas before the official auditor does.
A typical gap analysis involves:
- Reviewing your firewall rules and configurations.
- Checking the patch levels on a sample of devices.
- Verifying user access controls and administrator privileges.
- Testing the effectiveness of your malware protection.
This process provides a clear action list of everything that needs fixing, turning potential audit roadblocks into a manageable to-do list.
Step 3: Remediation Work
Your gap analysis will leave you with a clear list of remediation tasks. Now it’s time to get hands-on and resolve those issues. This might involve updating old software, tightening firewall configurations, removing excessive user permissions, or implementing new security tools.
This is often the stage where organisations find immense value in seeking expert help. A team that understands the certification process inside and out can ensure that fixes are implemented correctly and efficiently, avoiding frustrating delays. Navigating these technical hurdles is a core function of well-structured managed services, providing the skills and resources to close security gaps effectively.
Think of remediation as the study period before a major exam. It’s your opportunity to address all the challenging subjects and walk into the test fully prepared.
Step 4: Selecting a Certification Body and Undergoing the Audit
Once all remediation work is complete, you are ready for the formal audit. You'll need to choose an IASME-accredited Certification Body (CB) to carry out the assessment. They will schedule the technical audit, which includes the external vulnerability scan and the internal tests on your sample devices.
The auditor will work through the five controls, verifying that your systems meet the required standard. With proper preparation, this should feel like a straightforward confirmation of the hard work you’ve already invested. After passing, you’ll be awarded your Cyber Essentials Plus certificate, which is valid for 12 months.
Common Questions About Cyber Essentials Plus
Navigating the details of any certification can bring up many questions. To help you make a fully informed decision, we’ve put together clear, straightforward answers to the most common queries we hear from businesses exploring Cyber Essentials Plus.
This section is designed to cut through the jargon and provide the practical information you need to move forward with confidence.
Do I Need to Get Cyber Essentials Basic First?
This is a common point of confusion, but the answer is refreshingly simple: No, not usually.
Most accredited certification bodies bundle the basic self-assessment questionnaire (SAQ) into the Cyber Essentials Plus process. You first complete and pass the SAQ, which satisfies the requirement for the basic certificate. This then opens a three-month window for you to complete the hands-on technical audit for the 'Plus' certification. It’s an integrated approach that is ideal for organisations that already know they want the higher level of assurance.
What Is the Typical Cost for Cyber Essentials Plus?
Unlike the basic certification, which has a fixed price, the cost for a Cyber Essentials Plus audit is more variable. The final price depends on the size and complexity of your IT environment, as that directly impacts the time and effort required from the auditor.
For a small to medium-sized business, you can generally expect the audit itself to range from £1,400 to £2,500.
It's crucial to remember that this figure only covers the audit fee. You should also budget for any potential remediation needed to bring your systems up to standard, as well as any expert support you might engage to prepare for the assessment.
Planning for these potential costs upfront prevents surprises and contributes to a smoother certification journey.
What Happens If We Fail the Audit?
Failing an audit isn’t the end of the road; think of it as a valuable, guided health check. A failure simply means the auditor has found one or more issues that do not meet the standard and need to be addressed.
After the initial audit, the certification body will provide a detailed report pinpointing exactly what went wrong. You'll then get a remediation window—typically around 30 days—to fix the identified problems. Once the issues are resolved, the auditor will re-test only the specific controls that failed. This focused re-assessment saves both time and money. Having a responsive IT partner at this stage can be invaluable, helping you close those technical gaps quickly to ensure you pass the second time around.
How Long Does the Certification Last?
Both Cyber Essentials and Cyber Essentials Plus certifications are valid for 12 months from the date they are issued. This annual renewal is a core part of the scheme's design for good reason.
Cyber threats are constantly evolving, with new vulnerabilities and attack methods emerging all the time. An annual re-certification ensures your security measures remain current, effective, and aligned with the latest defensive standards. It reinforces the vital principle that good cyber security isn't a one-time project but an ongoing commitment. Renewing each year sends a powerful message that your dedication to protecting your business and client data is consistent and up-to-date.
Achieving Cyber Essentials Plus is a powerful statement about your commitment to security, but it requires careful preparation and technical expertise. At ZachSys IT Solutions, we provide the strategic guidance and hands-on support to get your systems audit-ready, helping you achieve certification smoothly and build a truly resilient IT foundation for the future.



