Subtotal $0.00
Infrastructure as Code (IaC) is a transformative approach to managing and provisioning IT infrastructure—servers, networks, databases, and more—through machine-readable definition files, rather than manual configuration or interactive tools. It’s a foundational DevOps practice that treats your infrastructure with the same discipline as application software, enabling you to version, test, and deploy your environment with precision, speed, and reliability.
From Manual Clicks to Automated Blueprints
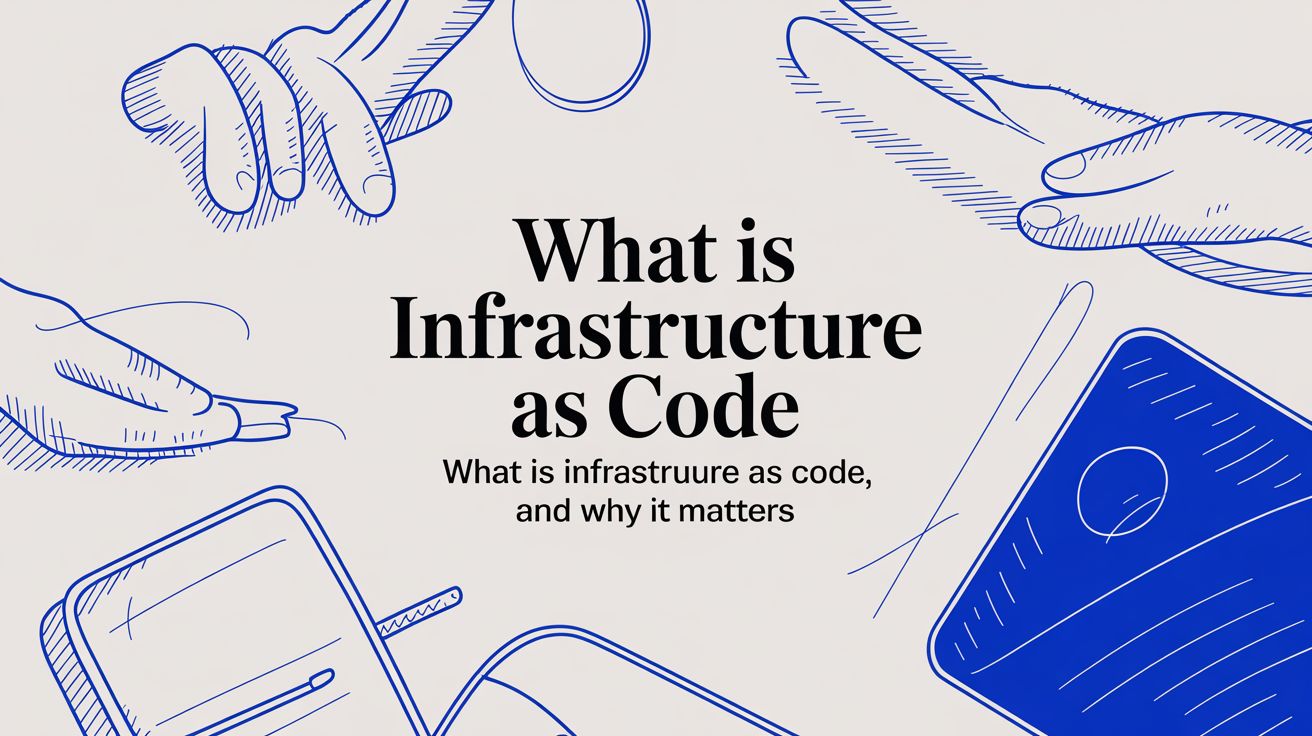
Imagine a systems engineer needs to launch a new environment. Traditionally, this involved logging into a cloud provider's portal and manually clicking through dozens of screens to provision servers, configure network rules, and install necessary software. This process is not only slow and laborious but is also a breeding ground for human error. If you need ten identical servers, can you guarantee every single one is configured the same? What happens during a disaster recovery scenario when you must rebuild everything from memory or scattered documentation?
This manual method is like building a house brick-by-brick without a definitive blueprint. You might end up with a functional structure, but it’s nearly impossible to replicate perfectly or scale efficiently. Over time, small, undocumented manual adjustments lead to configuration drift, where development, staging, and production environments slowly diverge. This drift is a common cause of bizarre, hard-to-diagnose failures that can bring operations to a halt.
The Blueprint Approach of IaC
Infrastructure as Code introduces a more intelligent, repeatable methodology. Instead of pointing and clicking, you define your entire technology stack in code, creating a detailed, automated blueprint. This definition file specifies every server, load balancer, database, and network rule your application requires to function.
It’s the equivalent of having a precise architectural plan for your entire IT system. This plan is:
- Version Controlled: The code is stored in a repository like Git, allowing you to track every change, collaborate on modifications with your team, and instantly roll back to a previously known good state if an issue arises.
- Automated: Once the blueprint is defined, automated tools can execute it consistently, time after time. This eliminates manual toil and guarantees that every environment is an exact, predictable replica.
- Testable: Just like application code, your infrastructure definitions can be validated and tested before they are ever deployed, catching potential configuration errors early in the development lifecycle.
This paradigm transforms infrastructure from a rigid, manually-managed asset into a dynamic, software-defined system. It ceases to be a siloed IT function and becomes an integrated component of your business's value delivery pipeline.
By treating infrastructure as code, organisations establish a single source of truth for their environments. This not only accelerates deployments but also builds a reliable, auditable, and secure foundation for business growth.
The ultimate goal is to achieve consistency and reliability at any scale. Whether you're spinning up a temporary testing environment or deploying a major production workload for thousands of users, the process becomes fast, predictable, and free from the costly inconsistencies of manual setups. This is the core business value of Infrastructure as Code—transforming brittle, hand-crafted systems into robust, automated ones. Successfully navigating this shift often benefits from experienced guidance, ensuring best practices are embedded from the start to build a scalable and resilient foundation.
Understanding Declarative vs Imperative IaC
When exploring Infrastructure as Code, you will inevitably encounter two fundamental approaches to writing your blueprints: declarative and imperative. Understanding the distinction is critical, as it's not just a technical detail—it shapes how you manage change, handle complexity, and reason about your entire cloud environment.
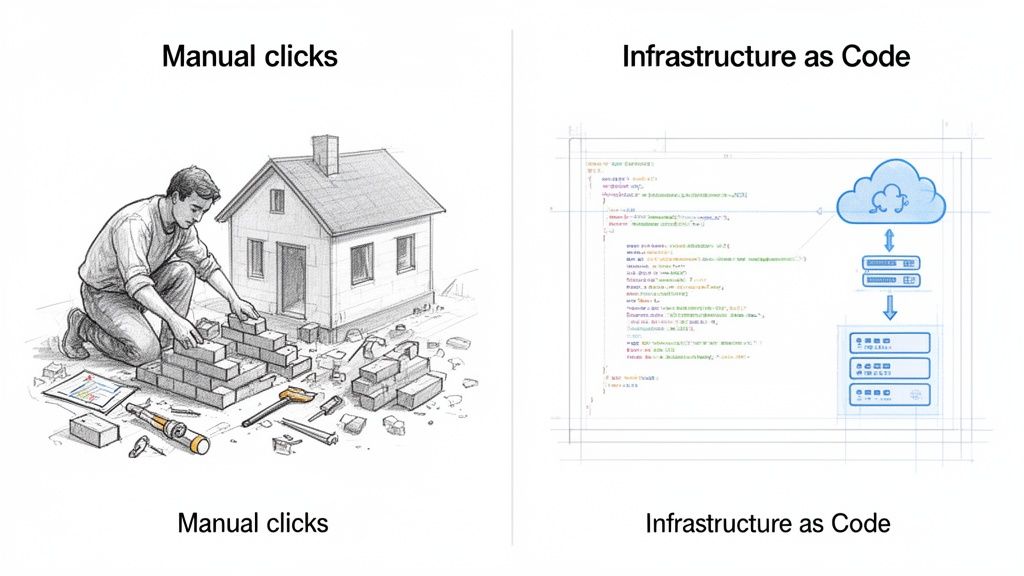
A simple analogy is ordering a pizza.
The declarative approach is like telling the restaurant, "I want a large pepperoni pizza with extra cheese." You describe the desired final state, but you don’t specify how the chef should make it. The sequence of spreading the sauce or layering the toppings is the chef's concern. Your focus is on the end result.
Conversely, the imperative approach is like giving the chef a detailed recipe: "First, preheat the oven to 220°C. Second, roll the dough to 12 inches. Third, spread two ladles of tomato sauce…" You are specifying the exact sequence of commands required to reach the final state.
The Declarative Approach: Defining the 'What'
The declarative model has become the industry standard for modern IaC, and for good reason. Tools like Terraform, AWS CloudFormation, and Azure Bicep operate on this principle. You define the desired state of your infrastructure—for example, "I need two virtual machines of this size, one load balancer, and a database." The tool then determines the most efficient way to achieve that state.
The key advantage here is idempotency. When you run the declarative code, the tool intelligently compares the current live state with your desired state. If they match, it does nothing. If a server is missing, it creates it. If a network setting is incorrect, it corrects it. This guarantees a predictable outcome and prevents configuration drift without requiring you to write complex logic to handle every possible starting condition.
At its core, declarative IaC is about focusing on the outcome, not the process. This abstracts away significant complexity, allowing the tooling to manage the heavy lifting of creating, updating, or deleting resources to match your definition.
The Imperative Approach: Defining the 'How'
The imperative approach, by contrast, gives you explicit control. You write scripts that execute a precise sequence of commands. Tools like Ansible can be used imperatively, as can general-purpose scripting languages like PowerShell or Bash. You have complete, granular control over how the final state is achieved.
This level of control can be invaluable for complex, multi-step deployments or when a specific order of operations is critical. However, the trade-off is that the burden of managing state falls on you. Your script must include logic to check if a resource already exists before attempting to create it, making the code more complex and harder to maintain over time.
Comparing the Two Models
This table summarises the key differences in a real-world context.
Declarative vs Imperative IaC Approaches Compared
| Attribute | Declarative ('What') | Imperative ('How') |
|---|---|---|
| Focus | Defines the desired end state of the infrastructure. | Specifies the sequence of commands to reach the end state. |
| Idempotency | Naturally idempotent; re-running the code ensures the state matches the definition. | Requires explicit logic to handle existing resources and achieve idempotency. |
| State Management | Tools often manage a state file to track resources and plan changes. | State is not explicitly tracked; relies on the current live environment. |
| Learning Curve | Simpler to start for defining resources, but requires understanding the tool's logic. | Steeper curve as it requires scripting skills and manual handling of complex logic. |
| Common Tools | Terraform, Bicep/ARM, CloudFormation, Pulumi. | Ansible (can be declarative too), Chef, custom scripts (PowerShell, Bash). |
Ultimately, choosing between declarative and imperative isn’t about one being universally "better." The decision depends on your team's skills, your project's requirements, and the level of control you need.
For most cloud infrastructure management today, the declarative model is preferred for its simplicity, predictability, and reliability. That said, a deep understanding of both paradigms is crucial for building a truly flexible and robust automation strategy. Many organisations find that a pragmatic blend of approaches, guided by experienced IT partners, delivers the most powerful and sustainable business outcomes.
Navigating the Modern IaC Toolkit
Choosing the right Infrastructure as Code (IaC) tool is like selecting the right power tool for a major construction project. While many can perform the same basic function, each is engineered with a specific purpose, platform, and workflow in mind. The tool you select will fundamentally shape your team's processes, influence your platform dependencies, and impact your ability to collaborate effectively.
This is not merely a technical decision; it's a strategic one that must align with your business objectives. Are you pursuing a multi-cloud strategy to avoid vendor lock-in, or are you committed to leveraging the deep, seamless integration of a single cloud provider? The increasing weight of this decision is reflected in market trends.
The UK's Infrastructure as Code market, for instance, was valued at USD 59.0 million in 2023 and is projected to grow to USD 239.6 million by 2030. This rapid expansion, driven by a 22.2% compound annual growth rate, highlights how seriously businesses are investing in automated infrastructure. You can explore these projections further in the report from Grand View Research.
The Cloud-Agnostic Champion: Terraform
For any organisation operating across multiple cloud platforms—such as a mix of Azure, AWS, and Google Cloud—Terraform from HashiCorp is often the default choice. It functions as a universal translator for infrastructure, allowing you to use a single, consistent language (HCL) to provision resources from hundreds of different providers.
This cloud-agnostic capability is its defining feature. Instead of your team needing to learn a separate tool for each platform, they can master one. This creates a unified workflow that simplifies management and reduces operational complexity, making it an ideal fit for businesses that prioritise flexibility and want to keep their options open.
Platform-Native Powerhouses: AWS CloudFormation and Azure Bicep
In many cases, however, deep integration within a single cloud ecosystem is more valuable than multi-cloud flexibility. For these scenarios, platform-native tools are often the superior choice.
-
AWS CloudFormation is the original IaC solution for Amazon Web Services. It offers unparalleled integration with every AWS service, ensuring that new features and capabilities are supported from day one. If your entire operation is built on AWS, CloudFormation provides the most seamless and powerful way to manage your infrastructure.
-
Azure Bicep is Microsoft's modern, domain-specific language for deploying Azure resources. It was designed to simplify the authoring experience and overcome the verbosity of its predecessor, ARM Templates, by offering a cleaner syntax and more transparent abstractions. For teams fully invested in the Azure ecosystem, Bicep is the most direct and efficient path to defining and deploying infrastructure.
The choice between a cloud-agnostic tool like Terraform and a native one like Bicep is not about which is "better." It's about aligning your tools with your cloud strategy. A multi-cloud business benefits from Terraform's versatility, while an Azure-centric organisation gains speed and simplicity with Bicep.
Bridging Gaps with Ansible and Pulumi
The IaC landscape extends beyond just provisioning core infrastructure. Two other tools play distinct yet critical roles in a modern technology stack.
Ansible excels at configuration management—the process of installing software, applying patches, and managing the state of systems after they have been provisioned. To use an analogy: if Terraform builds the house, Ansible furnishes it. Its simple, agentless architecture and YAML-based playbooks make it exceptionally effective for automating application deployments and ongoing system administration.
Pulumi offers a unique value proposition for development teams by allowing them to define infrastructure using familiar programming languages like Python, TypeScript, or Go. This approach blurs the line between application and infrastructure code, empowering developers to leverage existing skills and tools—such as loops, functions, and classes—to build their environments. For organisations where developers have a hands-on role in infrastructure, Pulumi can significantly lower the barrier to entry. This is especially relevant as more organisations adopt containerisation; you can learn more about how IaC principles intersect with container management in our detailed guide.
Ultimately, selecting the right tool depends on your unique context—your cloud provider, your team's skillset, and your long-term strategic vision. A clear understanding of these leading options is the first step toward building an infrastructure that is scalable, manageable, and prepared for future challenges.
How an IaC Workflow Operates in the Real World
Understanding the theory is one thing, but seeing Infrastructure as Code (IaC) in a real-world workflow truly reveals its power. A well-designed IaC process isn't an abstract exercise; it fundamentally reshapes how teams build, test, and release infrastructure by integrating it directly into the software development lifecycle.
Let's walk through a typical scenario. Imagine your development team needs to deploy a new web application on Microsoft Azure. Instead of navigating the Azure portal to manually create resources, they begin by defining the entire environment in a code file using a tool like Azure Bicep.
This Bicep file becomes the single source of truth. It explicitly declares everything the application needs to run: the App Service Plan for hosting, the SQL database for data persistence, the virtual network for secure communication, and a storage account for static assets. Every component is captured as code.
From Code to Cloud: The CI/CD Pipeline
Once the Bicep code is written, it is committed to a central Git repository, just like application code. This step is crucial, as it provides a complete, auditable history of every change, making it simple to track who changed what, when, and why—and to roll back if necessary.
This commit then triggers a Continuous Integration/Continuous Deployment (CI/CD) pipeline, typically managed by a tool like Azure DevOps or GitHub Actions. This pipeline is the automated engine that transforms your code into live, functioning infrastructure.
A typical IaC pipeline executes the following automated stages:
- Validation (Linting): The pipeline first performs static code analysis on the Bicep file. This is an automated check for syntax errors, adherence to best practices, and potential security vulnerabilities before a deployment is even attempted.
- Pre-flight Check (Plan/What-If): Next, the pipeline executes a "what-if" deployment. This command simulates the entire deployment against the target Azure environment without making any actual changes. It generates a detailed plan showing exactly which resources will be created, modified, or deleted, giving a human reviewer a final opportunity to approve the changes.
- Deployment (Apply): Once the plan is approved, the pipeline proceeds with the actual deployment. The IaC tool communicates with the Azure API and provisions all resources precisely as defined in the Bicep file, eliminating manual steps and guesswork.
- Post-deployment Testing: Finally, automated tests can be run against the newly created environment to verify that the application is running correctly and all components are configured as expected.
This entire process delivers a consistent, repeatable, and transparent method for managing infrastructure. It also illustrates how your choice of IaC tool must align with your cloud strategy, whether you are managing a multi-cloud estate or are deeply integrated with a single provider.
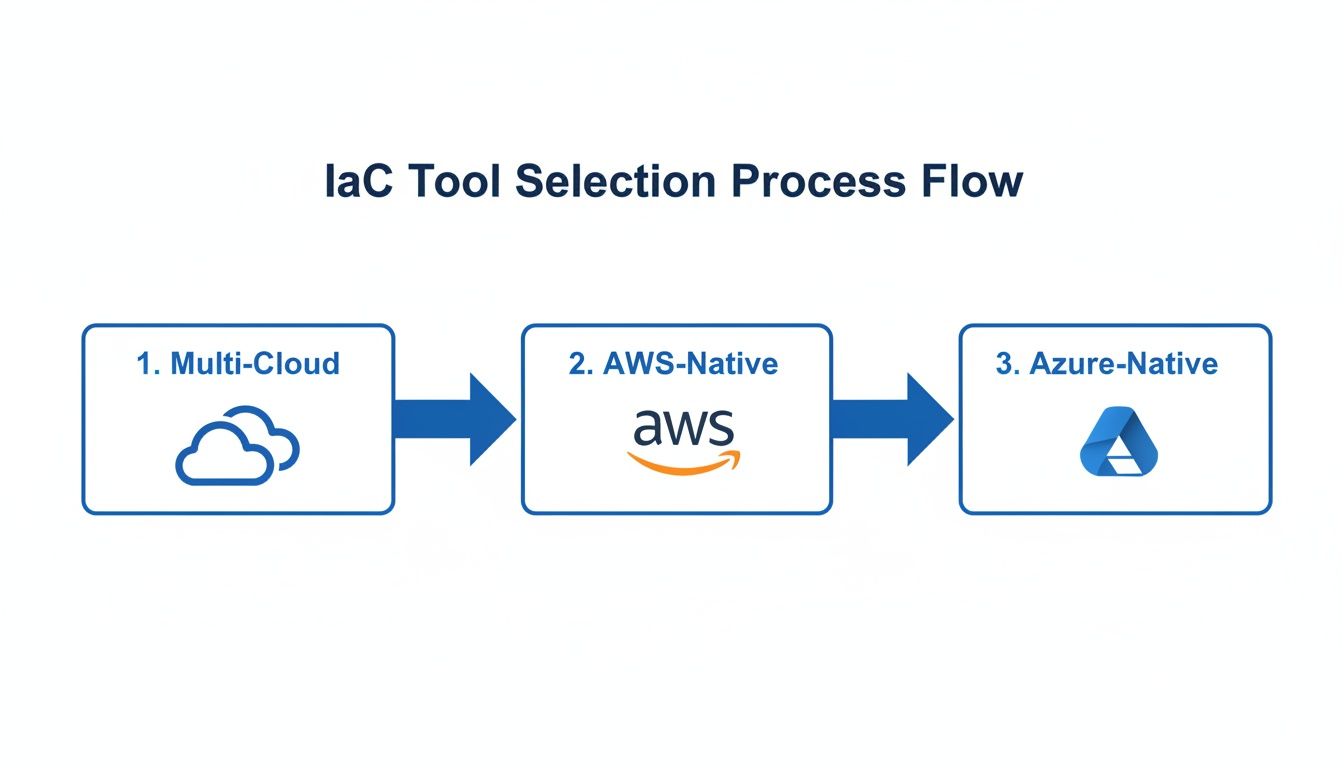
The flowchart above helps visualize this strategic decision-making process, highlighting the choice between a tool designed for multi-cloud flexibility and one optimised for deep integration with a native platform like AWS or Azure.
The Value of an Automated Workflow
This end-to-end workflow embodies the core philosophy of IaC: a systematic, software-driven approach to infrastructure management. It shifts the paradigm from the inherent risks of manual configuration to a robust, automated framework that is both fast and reliable.
By integrating infrastructure changes into a version-controlled, automated pipeline, organisations create a system that is not only efficient but also inherently more secure and auditable. Every change is documented, reviewed, and tested, reducing configuration drift and strengthening operational stability.
Achieving this level of automation requires careful planning and the right expertise. Implementing and optimising these pipelines is a core part of effective DevOps consulting, where strategic guidance helps organisations build scalable and resilient systems from the ground up. The result is a powerful, dependable mechanism for managing technology at any scale.
Embedding Security and Compliance into Your Code
In traditional IT environments, security and compliance checks often occur at the end of the development cycle—a manual review gate that teams must pass just before going live. This reactive approach is not only slow but also risky, as it identifies problems when they are most difficult and expensive to fix.
Infrastructure as Code (IaC) fundamentally changes this dynamic by "shifting security left." It enables you to integrate security and compliance directly into your development workflow, making them an intrinsic part of your infrastructure's DNA rather than an afterthought.
Introducing Policy as Code
One of the most powerful concepts enabling this shift is Policy as Code. This practice involves defining your organisation's security and compliance rules in a simple, human-readable language that can be checked automatically.
Tools like Open Policy Agent (OPA) allow you to write clear rules, such as, "No virtual machine can have a public IP address unless it is part of a specific security group," or "All storage accounts must have encryption enabled."
These policies are then integrated directly into your CI/CD pipeline. Before any infrastructure code is deployed, it is automatically scanned against this rulebook. If a developer attempts to commit code that violates a policy, the pipeline halts, provides immediate feedback, and prevents the non-compliant infrastructure from ever being created.
The Power of Immutable Infrastructure
IaC also promotes the concept of immutable infrastructure. Traditionally, if a server required a security patch or a configuration update, an administrator would log in and apply the change directly. Over time, these manual modifications lead to configuration drift, creating inconsistencies and hidden security vulnerabilities.
Immutable infrastructure advocates for a different model: you never modify a running server.
Instead of patching or updating existing servers, you simply deploy new, updated versions from your code templates and then terminate the old ones. This "replace, don't repair" strategy drastically reduces the attack surface and eliminates configuration drift entirely.
Because every server is built from a trusted, version-controlled source, you can be confident that your entire environment is consistent and compliant with your security standards.
Building a Bulletproof Audit Trail
For any organisation subject to strict regulatory standards like GDPR or ISO 27001, proving compliance is non-negotiable. The version-controlled nature of IaC provides a complete, transparent, and immutable audit trail of every change made to your infrastructure.
Every modification is logged in your Git history, clearly showing who made the change, what was altered, and when it was approved. This not only makes audits significantly less painful but also provides concrete evidence that your security controls are being enforced consistently. A detailed review, such as a formal Azure security assessment, becomes a much more straightforward process when all configurations are documented as code.
The broader shift to cloud computing, where IaC thrives, has accelerated the adoption of these advanced security practices. Data from the Office for National Statistics shows that cloud technology adoption reached 69% among UK firms in 2023, creating an ideal landscape for IaC to automate and secure these expanding cloud estates.
Getting Started with IaC: First Steps and Best Practices
Adopting Infrastructure as Code can seem daunting, but it becomes far more manageable with a pragmatic, iterative approach. Instead of attempting a "big bang" migration, the most effective strategy is to start small. Select a non-critical project to serve as a pilot.
This first project is your learning ground—a low-risk environment where your team can become familiar with the tools, processes, and mindset required for IaC. Your initial focus should be on creating modular and reusable code. Avoid writing a single, monolithic file for your entire environment. Instead, think in components: a module for networking, another for compute resources, and another for your database. This modular approach pays significant dividends, making your infrastructure easier to manage, update, and scale over time.
Building a Solid Foundation
Once you are comfortable with the basics, it is essential to establish and codify your standards. This includes defining consistent naming conventions, resource tagging strategies, and a standardized folder structure for your projects. Documenting these guidelines is crucial for maintaining a clean, predictable, and scalable IaC codebase as your team grows and more projects are brought under IaC management.
A critical part of this foundation is secure secrets management. One of the most common—and dangerous—mistakes is hard-coding sensitive information like API keys or database passwords directly into configuration files. This practice creates a significant security vulnerability.
Using a dedicated secrets management tool is not optional; it is essential for any production-grade IaC implementation. Services like Azure Key Vault or AWS Secrets Manager allow you to store credentials securely and reference them dynamically in your code without ever exposing them in plaintext.
Avoiding Common Implementation Pitfalls
Beyond mishandling secrets, another common pitfall arises when teams begin to collaborate: improper state file management. Declarative tools like Terraform rely on a state file to map the code to real-world resources. Without a robust system for managing this file, two engineers could attempt to apply changes simultaneously, leading to a corrupted state file and an infrastructure that is out of sync with your code.
Here are a few best practices to sidestep these common issues:
- Use Remote State Backends: Never store the state file on a local machine. Use a shared, remote backend like an Azure Storage Account or an Amazon S3 bucket to create a single source of truth for the entire team.
- Enable State Locking: Most remote backends support state locking. This feature ensures that only one
applyoperation can run at a time, preventing conflicts and protecting the integrity of your state file. - Version Everything: Treat your IaC with the same discipline as application code. Store all configurations, modules, and variable files in a Git repository to maintain a complete change history and the ability to roll back if needed.
Establishing a robust IaC foundation is about more than just writing code; it's about building solid processes and guardrails from day one. These early decisions often benefit from structured IT guidance, ensuring that the systems you build are secure, scalable, and engineered for long-term success.
Answering Your Questions About IaC
As teams begin their journey with Infrastructure as Code, several common questions naturally arise. Here are straightforward, practical answers to some of the most frequent points of confusion.
How Is IaC Different from Configuration Management?
This is a frequent point of confusion, but the distinction is quite clear when viewed through an analogy.
Think of building a new house. Infrastructure as Code is the blueprint and the construction crew—it provisions the foundation, erects the walls, and installs the roof. Configuration management, on the other hand, is the interior design team. They arrive after the house is built to install appliances, configure the Wi-Fi, and arrange the furniture.
IaC tools like Terraform or Bicep excel at provisioning core infrastructure resources—servers, networks, and databases. Then, configuration management tools like Ansible take over to manage the software and state inside those resources, such as installing applications or applying security patches. They are not competing technologies; they are complementary and work best together.
Can IaC Be Used for On-Premises Data Centres?
Absolutely. While IaC rose to prominence with the cloud, its principles and benefits are equally applicable to on-premises infrastructure. Many leading IaC tools, particularly Terraform and Ansible, provide extensive support for managing a wide range of on-premises hardware, from VMware vSphere and Cisco networking equipment to bare-metal servers.
This capability allows organisations to create a single, unified workflow to manage their entire hybrid estate. You can apply the same version control, testing, and automation practices to both your cloud and on-premises infrastructure, breaking down operational silos and improving consistency.
The core value of Infrastructure as Code lies in the automation, consistency, and repeatability it delivers. It doesn't matter where your hardware resides; IaC brings a software-driven methodology to any environment you manage.
What Is the Biggest Challenge When Adopting IaC?
The biggest hurdle in adopting IaC is often cultural, not technical. The transition requires a significant mindset shift for traditional infrastructure teams, moving them from a world of manual changes and reactive support tickets to a proactive workflow centered on code, version control, and automation.
This involves more than just learning a new tool like Git. It requires embracing CI/CD pipelines, collaborating more closely with developers, and adopting a software engineering discipline for infrastructure management. Without strong leadership, clear standards, and a well-planned adoption strategy, teams can become overwhelmed, leading to inconsistent implementations and technical debt. Addressing the people and process aspects is just as critical as selecting the right technology.
How Does IaC Support a Multi-Cloud Strategy?
IaC is not just beneficial for a multi-cloud strategy; it is a fundamental enabler. Cloud-agnostic tools like Terraform are game-changers in this context. They provide a common language and workflow to manage resources across disparate cloud providers, whether it's Azure, AWS, or Google Cloud.
This creates a powerful abstraction layer, freeing your organisation from vendor lock-in and the need to maintain expertise in multiple platform-specific toolsets. Your team can master one set of tools and processes and then deploy workloads to the cloud provider that best fits the needs of a given application. This dramatically simplifies operations and provides true strategic flexibility.
Ready to move beyond manual processes and build a truly automated, scalable, and resilient infrastructure? The journey to effective Infrastructure as Code starts with a clear strategy and expert guidance. Zachsys IT Solutions provides the DevOps consulting and structured IT support needed to build future-ready systems, ensuring your implementation is secure, efficient, and aligned with your business goals.
Book a free, no-obligation consultation to discuss how we can help you build a robust IaC foundation. Learn more about our services at https://zachsys.com.