Subtotal $0.00
Think of cyber security managed services as hiring an elite, 24/7 security team for your digital infrastructure. It’s a world away from simply installing security software and hoping for the best. This outsourced team actively monitors your systems, patrols your digital perimeter, and responds the moment a threat appears—a strategic approach that transforms cyber security from a reactive headache into a proactive, expert-managed function.
For any business that cannot justify the significant cost of an in-house security operations centre, this model provides an effective and scalable solution.
Why Outsourcing Security Is Now a Strategic Necessity

In the past, many organisations approached cyber security with a simple checklist: install a firewall, run antivirus software, and hope for the best. That passive approach is no longer viable. Today’s threats are more persistent, sophisticated, and often automated, meaning a breach is often a matter of ‘when,’ not ‘if.’
The real challenge isn't just stopping attacks; it's identifying and neutralising them before they can cause significant damage. This is precisely where cyber security managed services add value. By partnering with a managed security service provider (MSSP), you gain immediate access to a dedicated team of specialists whose sole purpose is to protect your digital assets around the clock.
A managed security service provider doesn't just sell you tools; they deliver a security outcome. They shoulder the operational burden of 24/7 monitoring, threat hunting, and incident response, freeing your internal team to focus on core business objectives.
The Driving Forces Behind Managed Security
This shift toward outsourcing is driven by practical business realities. First, there’s a massive global shortage of qualified cyber security professionals. Attempting to build an internal Security Operations Centre (SOC) from scratch is incredibly expensive, involving significant investment in talent, continuous training, and technology.
This economic reality is reflected in market growth. The UK's managed services market for cyber security is projected to generate US$1.89 billion in revenue by 2025. This surge is fuelled by escalating threats, the complexities of hybrid work, and increasing regulatory pressures like GDPR and the push for certifications such as Cyber Essentials. You can explore these market dynamics further with recent industry analysis.
Ultimately, partnering with an MSSP offers a more predictable and scalable financial model. Instead of large capital expenditures on equipment and staff, you have a recurring operational cost that provides access to:
- Enterprise-Grade Technology: Leverage advanced security tools without the prohibitive cost of ownership.
- Specialised Expertise: Instantly access a deep bench of security analysts, threat hunters, and incident response experts.
- Proactive Defence: Transition from a reactive, "break-fix" posture to a forward-thinking strategy built on continuous monitoring and threat mitigation.
Engaging a provider of cyber security managed services is no longer a luxury—it’s a fundamental component of modern business resilience. For most organisations, it is simply the most effective way to build a secure and scalable operational environment.
The Core Components of Managed Security Services
Managed cyber security isn't a single product; it's a suite of coordinated defences and expert services. Think of it like a modern hospital. You don't rely on one doctor; you have specialists in diagnostics, emergency response, and preventative care collaborating to maintain your health. Similarly, a managed security provider layers multiple services to build a comprehensive shield around your business.
Each component addresses a specific business challenge, from spotting hidden threats to managing the digital perimeter of your network. Understanding these individual parts helps clarify the bigger picture and determine which services are most critical for your operations.
The Human Element: Managed Detection and Response (MDR)
At the heart of any effective security strategy is human intelligence. Managed Detection and Response (MDR) provides exactly that. While automated tools are excellent at flagging potential issues, they often lack the context to distinguish a real threat from a false alarm. MDR services provide a team of security analysts who investigate alerts 24/7, hunt for hidden threats, and take decisive action to contain and neutralise attacks.
This service directly solves the problems of alert fatigue and the cyber security skills gap. Instead of your IT team being inundated with thousands of notifications, MDR experts perform the heavy lifting, ensuring genuine threats are addressed quickly before they can cause significant damage.
The Central Hub: Security Operations Centre as a Service (SOCaaS)
If MDR is the elite response team, the Security Operations Centre (SOC) is the command centre where all intelligence is gathered and analysed. SOC-as-a-Service (SOCaaS) gives your organisation access to a fully-staffed, enterprise-grade security hub without the multimillion-pound investment required to build one from scratch.
A SOCaaS team centralises security monitoring, using advanced tools to gain a complete view of your entire IT estate. This solves a major visibility problem for many businesses, allowing them to spot correlated attack patterns across different systems that might otherwise go unnoticed.
The true value of SOCaaS lies in turning raw security data into actionable intelligence. It connects the dots between a suspicious login, unusual network traffic, and an endpoint alert to identify a coordinated attack in progress.
Core Defensive Layers
Beyond the human-led functions, several key services form the backbone of any managed security offering. These are the essential building blocks for creating a robust defensive posture.
Here’s a breakdown of the most common services and the business problems they solve.
Key Managed Security Services and Their Business Functions
| Service Component | Core Function | Primary Business Problem Solved |
|---|---|---|
| Managed Firewalls | Expert configuration, continuous monitoring, and management of network firewalls. | Prevents unauthorised access and mitigates misconfigurations, a leading cause of breaches. |
| Vulnerability Management | Proactive scanning of systems to identify and prioritise known security weaknesses. | Reduces the overall attack surface by guiding the remediation of critical vulnerabilities. |
| Managed SIEM | Collection, aggregation, and expert analysis of log data from across the IT environment. | Provides deep visibility, aids in compliance reporting, and enables proactive threat hunting. |
These services ensure that your core defences are not just in place but are actively managed and optimised by experts who live and breathe security every day.
Responding When an Incident Occurs
Even with the best defences, a security incident can still happen. This is where Incident Response (IR) services become invaluable. A managed IR service provides a pre-agreed plan and an expert team on standby to manage a breach from detection through to recovery. They contain the threat, eradicate the attacker's presence, and restore normal operations as quickly as possible.
This structured approach avoids the chaotic and costly scramble that many businesses face after a breach. Having an IR plan guided by seasoned professionals significantly minimises both financial and reputational damage.
Many of these components align with modern security philosophies. You can learn more about how they fit into a proactive defence by exploring what is Zero Trust security. Ultimately, each of these services contributes to a layered defence where the failure of one control is backed up by another—a strategy focused on building resilient and future-ready systems.
The Strategic Business Benefits of Outsourced Security
Choosing to use cyber security managed services is not just a technical decision—it's a strategic business move that delivers tangible value far beyond the IT department. When security is treated as a managed outcome instead of an in-house burden, it unlocks significant financial and competitive advantages.
This shift helps your business move from a defensive, reactive posture to a proactive one. It’s about building resilience, earning customer trust, and creating a stable foundation for sustainable growth. The benefits are clear, measurable, and address some of the biggest challenges modern businesses face.
Overcoming the Cybersecurity Skills Gap
One of the most immediate benefits is access to a deep bench of security talent. The UK is facing a major cybersecurity skills shortage, which makes hiring, training, and retaining expert staff incredibly difficult and expensive.
Attempting to build an in-house Security Operations Centre (SOC) is a multimillion-pound commitment that requires constant investment in both people and technology. A managed security provider removes this massive barrier.
Partnering with a managed security service provider (MSSP) effectively addresses the talent crisis. It provides on-demand access to a team of certified analysts, threat hunters, and incident responders dedicated to protecting your business 24/7.
This diagram illustrates how a layered managed security approach works, with SOC-as-a-Service providing the central strategy that enables other specialised functions.
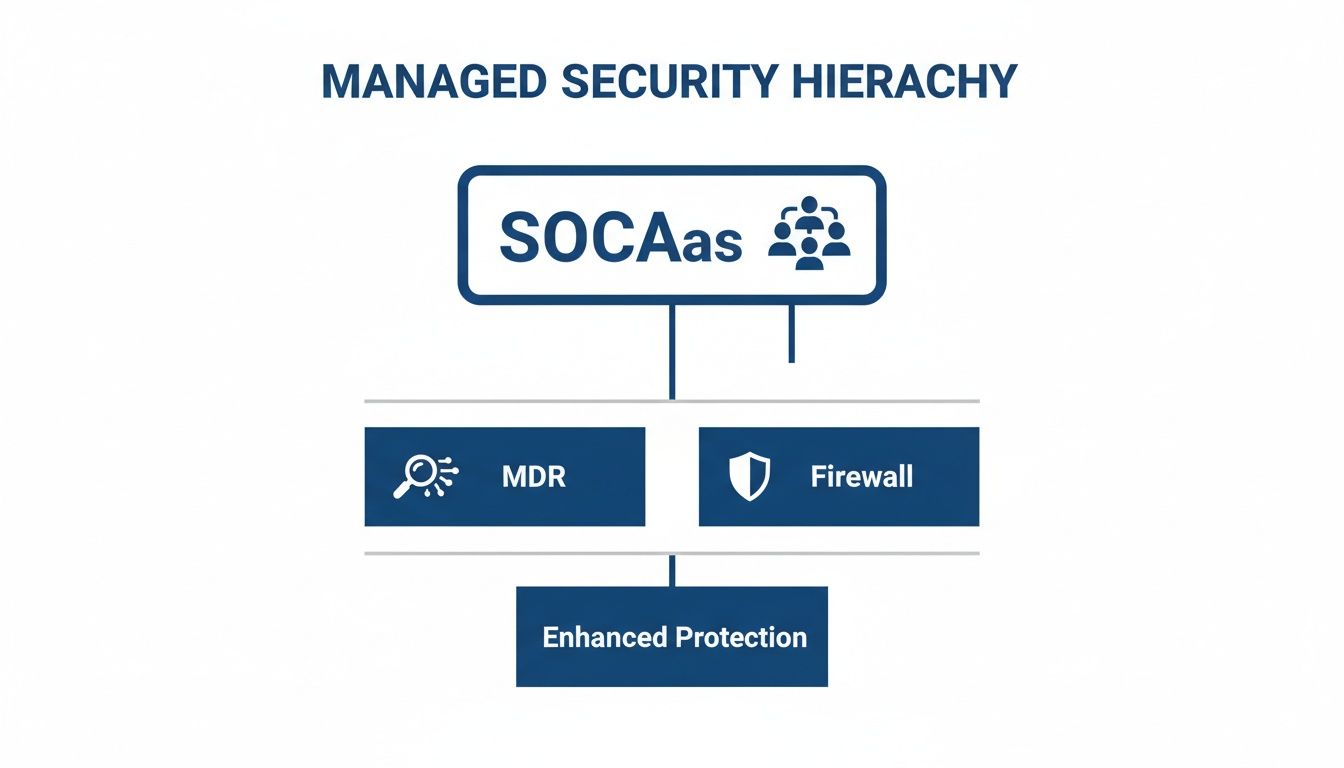
This structure demonstrates how specialised services like Managed Detection and Response (MDR) operate under the cohesive oversight of a central security team, ensuring your defence is integrated, not fragmented.
Achieving Cost Predictability and Superior ROI
It may seem counterintuitive, but outsourcing security is often more cost-effective than managing it in-house. An internal approach involves unpredictable spending on software, hardware, and licences, not to mention the high recurring costs of specialist salaries and continuous training.
In contrast, cyber security managed services convert these variable expenses into a predictable operational cost. This model provides access to enterprise-grade tools and expertise for a fraction of the ownership cost, delivering a clear return on investment. This financial predictability is a key reason why more SMBs are choosing managed services, avoiding large capital outlays in favour of a more manageable operational model.
Streamlining Regulatory Compliance
Maintaining compliance with regulations like GDPR and other industry standards is a complex, continuous effort. An experienced MSSP simplifies this process dramatically. They possess deep expertise in navigating various regulatory frameworks and can implement the necessary controls and monitoring to ensure you meet your obligations.
For many UK businesses, certifications like Cyber Essentials are essential for winning contracts, particularly in the public sector. A managed security partner can guide your organisation through the entire process, from the initial gap analysis to final certification. You can learn more by reading our complete guide on what Cyber Essentials certification is.
Enabling Scalability and Business Growth
As your business grows, its attack surface expands, and security needs become more complex. A key benefit of managed services is their inherent scalability. An MSSP can seamlessly adapt its services to match your growth, whether you're onboarding new employees, opening new offices, or migrating to the cloud.
This flexibility ensures your security posture remains robust without requiring disruptive and costly overhauls of your internal infrastructure. This agility is a significant market driver; the UK cybersecurity market is projected to reach USD 12.88 billion by 2025, with services like MDR growing rapidly to address the talent shortages and cost pressures that SMBs face. You can explore a full analysis of these market trends on Mordor Intelligence. With structured support, you can pursue growth opportunities with confidence, knowing your security can scale alongside you.
How to Choose the Right Managed Security Partner
Selecting a partner for managed cyber security is a critical decision. You are not just hiring another supplier; you are entrusting them with the protection of your most valuable digital assets. The right choice feels like a natural extension of your team, while the wrong one leads to friction, security gaps, and wasted investment.
To make an informed choice, you need to look beyond sales presentations and assess their capabilities, processes, and cultural fit. This comes down to asking specific questions that reveal how they operate, especially under pressure.
A genuine partner doesn't just sell a service. They provide a clear, strategic roadmap to improve your security posture and act as a trusted guide in a complex field.
First, Evaluate Their Technical Expertise and Certifications
A provider's qualifications are the first indicator of their quality and depth of knowledge. You must be confident their team has the skills to handle sophisticated, modern threats. Do not hesitate to inquire about the team’s credentials and the company’s operational standards.
You are looking for a healthy mix of individual and company-wide certifications. While individual qualifications demonstrate team competency, broader accreditations prove they have robust, repeatable processes.
Here’s what to ask about:
- Team Certifications: Do their analysts and engineers hold respected credentials like CISSP, CCIE Security, or CompTIA Security+? This provides a baseline of their individual expertise.
- Company Accreditations: Has the company undergone independent audits? Certifications like SOC 2 Type 2 are a significant indicator that their internal security controls have been rigorously tested.
- Framework Familiarity: How well do they understand UK-specific frameworks like Cyber Essentials or industry standards like ISO 27001 and PCI DSS?
These are not just badges for a website; they are evidence of a provider’s commitment to high standards in an industry where "good enough" is never sufficient.
Next, Scrutinise Their Technology and Integration Capabilities
The best team in the world is ineffective without the right tools. A potential partner’s technology stack is the engine that drives their services, so you need to understand what they use and—more importantly—how it will integrate with your existing environment. A provider insisting on a complete "rip and replace" of your current tools may not be the most flexible or cost-effective choice.
The goal is to find a partner whose technology enhances what you already have, filling gaps rather than creating overlaps and confusion.
A mature managed security provider builds their service around seamless integration. They should be able to ingest data from your existing systems—firewalls, cloud platforms, and endpoint agents—to create a single, unified view of your security posture.
This unified approach prevents dangerous security silos and ensures your partner has full visibility across your entire IT estate. When evaluating their technology, focus on interoperability—it’s key to a smooth and effective partnership.
Finally, Define Their Incident Response and SLAs
When an incident occurs, a fast, organised response is critical. This is where a potential partner’s value is truly tested. You need absolute clarity on their incident response (IR) process and the contractual guarantees that back it up, known as Service Level Agreements (SLAs).
An SLA is more than a legal document; it's a commitment. It clearly defines the expected response times for detecting, escalating, and remediating threats. Vague SLAs should be considered a major red flag.
Your evaluation should focus on these points:
- Detection Time: How quickly do they guarantee the identification of a potential threat after an alert is generated?
- Response Time: Once a threat is confirmed, how long until an analyst is actively investigating and containing it?
- Communication Protocol: Who is your primary contact during an incident? How and when will you receive updates?
- Remediation Support: What is their role in recovery? Do they assist with removing the threat and restoring systems, or do they only detect and notify?
A strong partner will have a well-documented IR plan and will walk you through it step-by-step. They will offer clear, measurable SLAs that provide confidence in their ability to act decisively when it matters most. That level of preparation distinguishes a basic vendor from a strategic security ally.
Understanding Pricing Models and the Onboarding Process
When considering a managed cyber security partner, two key questions inevitably arise: "How much will this cost?" and "What does the implementation process involve?" Obtaining clear, straightforward answers is the first step toward building a solid, long-term security partnership.
A reputable provider will be transparent about the investment and the implementation roadmap, so you know exactly what to expect. No surprises, just a clear plan forward.
How Providers Structure Their Pricing
Managed security services are typically priced using a few common models. There is no single "best" option—the right choice depends on your company's size, IT complexity, and budgeting preferences.
The goal is to find a structure that provides predictability and value.
Here’s a breakdown of common pricing models:
- Per-Device or Per-User Pricing: This is the most straightforward model. You pay a set monthly fee for each computer, server, or user being protected. It is easy to understand and scales predictably as your organisation changes.
- Tiered Packages: Many providers bundle services into different levels (e.g., Bronze, Silver, Gold). A basic tier might cover essentials like firewall management, while higher tiers could add advanced threat hunting, MDR, and compliance reporting. This simplifies decision-making by aligning service levels with pre-set packages.
- All-Inclusive (Flat-Fee) Pricing: This model is ideal for businesses that require budget stability. You pay one predictable monthly fee covering an agreed-upon suite of services. It converts security into a stable operational expense rather than a fluctuating cost.
The most important quality in any pricing model is predictability. A provider offering a clear, flat-fee structure removes the risk of fluctuating monthly bills and allows you to treat security as a fixed, manageable cost.
What Influences the Final Cost?
Beyond the pricing model, several factors will shape your final quote. Understanding these helps explain why there is no one-size-fits-all price and provides a better sense of the investment.
The scope of services is the biggest factor. Basic monitoring is one thing; a comprehensive package with a 24/7 Security Operations Centre, proactive vulnerability management, and hands-on incident response is entirely different.
Other key cost drivers include:
- Complexity of Your IT Environment: A simple, single-office setup is easier to secure than a company with multiple sites, remote workers, and a hybrid cloud infrastructure.
- Number of Endpoints and Users: The more assets that require protection, the more resources are needed for effective monitoring and management.
- Regulatory and Compliance Needs: If you operate in a regulated industry like finance or healthcare, meeting standards such as GDPR or PCI DSS requires specialised expertise and tools, which adds to the cost.
The Onboarding Journey: A Step-by-Step Guide
Once you have selected a partner, the onboarding process begins. This is not an instantaneous switch-on but a carefully planned process to integrate their services into your environment with minimal disruption. A smooth onboarding is the foundation of a successful partnership.
While specifics may vary, the journey typically follows four key stages:
- Envision and Align: The first phase is discovery. Your new partner will meet with your team to deeply understand your business priorities, identify current security gaps, and establish a shared plan for success.
- Build and Prepare: Next, the technical work begins. The provider's team deploys the necessary software agents and tools across your systems. They configure monitoring platforms and establish clear roles and responsibilities for seamless collaboration.
- Launch and Refine: This is the go-live stage. The new security systems are activated, tested, and fine-tuned in your live environment. Once everything is running smoothly, the provider formally assumes responsibility, and your security operations are officially in their hands.
- Optimise and Grow: A great security partnership is dynamic. Your provider should schedule regular reviews to assess your security posture, discuss emerging threats, and ensure the service continues to support your business goals as you evolve.
Building Your Path to a More Secure Future
The core message is simple: proactive, expert-managed security is no longer a "nice-to-have." It is the bedrock of modern business resilience. In a world where cyber threats evolve daily, the key takeaway is that you do not have to navigate this landscape alone.
Engaging a managed cyber security service allows you to transfer the heavy burden of defence from your internal team to dedicated specialists.
Gaining Clarity on Your Security Posture
Where do you begin? The logical first step is to gain an honest assessment of your current security posture. Start by identifying your most critical digital assets—from sensitive customer data to intellectual property.
Next, ask the tough questions. Where are our biggest blind spots? What would be the real-world impact if one of those areas were breached? For most businesses, answering these questions and implementing a robust defensive framework is a significant undertaking. This is where expert guidance provides the strategic insight needed to build a defence that is not just strong today but prepared for tomorrow.
Partnering with an experienced team provides more than just tools; it delivers a strategic roadmap. It helps you prioritise risks, make informed investments, and build a security culture that protects your entire organisation.
Taking Proactive Steps
Once you understand your vulnerabilities, you can begin to close the gaps. This proactive stance is what separates prepared organisations from compromised ones, especially concerning common but devastating attacks. For a deeper dive into specific defensive tactics, our guide on how to prevent ransomware attacks is packed with practical advice.
Ultimately, securing your business is a journey of continuous improvement. It demands the right combination of technology, consistent processes, and specialised expertise. By choosing the right partner, you are not just buying a service; you are investing in a resilient future that allows you to focus on growth with confidence and peace of mind.
Your Questions Answered
When first exploring cyber security managed services, it's natural to have questions. Let's address some of the most common inquiries from business leaders.
How Is an MSSP Different from Standard IT Support?
Think of it this way: your standard IT support team acts as the mechanics keeping your company's engine running smoothly day-to-day. They ensure your systems are operational and efficient.
An MSSP, on the other hand, is your dedicated security detail. Their entire focus is on identifying external threats, hunting for intruders, and responding the moment an attack occurs. It's a highly specialised skillset that goes far beyond typical IT management.
Can Small Businesses Really Afford This?
Absolutely. In fact, for most small and medium-sized businesses, partnering with an MSSP is far more cost-effective than attempting to build an in-house security team.
The salary for a single senior security analyst can easily exceed the annual cost of a comprehensive managed service.
By outsourcing, you gain an entire team of experts and access to enterprise-grade security tools for a predictable monthly fee. This delivers a much higher return on investment and avoids the significant upfront cost of establishing your own security operations centre.
What Industries Benefit Most from These Services?
While any business with digital assets is a potential target, some sectors face greater risk and regulatory pressure.
Industries such as financial services, healthcare, legal firms, and manufacturing are prime candidates due to the sensitive data they handle and strict compliance requirements like GDPR.
However, any organisation that relies on technology for its core operations will see a significant boost in resilience. It's about obtaining the structured support needed to secure your operations and build a defence that is ready for the future.
Building a resilient and secure operational environment is critical for long-term success. The expert team at ZachSys IT Solutions provides the strategic guidance and structured IT support organisations rely on to protect their critical assets. Book a no-obligation consultation to understand your security posture and explore your options. Learn more at https://zachsys.com.



