Subtotal $0.00
Think of IT managed security services as your on-demand, expert cybersecurity department. This model provides 24/7 monitoring and management of your entire security infrastructure, handled by a team of external specialists whose sole function is to shield your digital assets from a relentless tide of cyber threats.
What Are IT Managed Security Services?
Imagine your business is a fortress. You could attempt to build your defences from scratch—hiring guards, investing in surveillance technology, and training your own response team. This is a significant undertaking, demanding massive investment in people, tools, and continuous training just to keep pace with sophisticated threats.
Alternatively, you could partner with a professional security firm that already has elite teams, advanced technology, and round-the-clock operations ready to deploy. That’s the core concept behind IT managed security services. Instead of building a costly and complex internal security operations centre (SOC), you entrust your digital defence to a third-party specialist.
This strategic move shifts cybersecurity from a large capital expenditure (building it all yourself) to a predictable, manageable operational expense. It’s about gaining access to enterprise-grade security without the financial burden and administrative overload that comes with an in-house build.
The Shift Towards Outsourced Expertise
Modern cybersecurity has become so complex that it is nearly impossible for most small and medium-sized businesses (SMBs) to manage effectively in-house. The sheer volume of alerts, the necessity for specialist tools, and the chronic shortage of skilled security professionals create a perfect storm of vulnerability.
This is precisely why the market is shifting so dramatically. In the UK, the managed security services sector is the fastest-growing segment of the IT services market, projected to expand at a 9.38% CAGR through 2031. This isn't just a trend; it's a direct response to a hyper-active threat landscape and tightening regulations, making outsourced security a strategic necessity, not a luxury. You can find more details about the UK IT services market growth on mordorintelligence.com.
Managed security is no longer just about offloading tasks. It’s a strategic decision to embed world-class expertise and resilience directly into your business, allowing you to focus on growth with genuine peace of mind.
Partnering with a provider grants immediate access to a dedicated team focused solely on your protection. This frees up your internal IT staff to concentrate on strategic projects that drive the business forward, rather than being bogged down in the constant, reactive fight against cyber threats. Organisations often rely on structured IT support to build a more secure and future-ready foundation.
Core Functions of Managed Security Services
At their heart, all IT managed security services are designed to perform critical functions that most businesses struggle to maintain consistently on their own. This table breaks down what these services do and why each function matters for your business.
| Core Function | Business Benefit |
|---|---|
| 24/7 Threat Monitoring & Detection | Proactively identifies and alerts on suspicious activity before it can cause damage, ensuring threats are caught at any time of day or night. |
| Security Incident Response | Provides immediate, expert-led action to contain and eliminate threats, significantly reducing the impact and cost of a potential breach. |
| Vulnerability Management | Continuously scans and assesses systems for weaknesses, helping you prioritise and fix security gaps before attackers can exploit them. |
| Security Device Management | Manages and optimises critical security tools like firewalls and intrusion detection systems, ensuring they are always configured correctly and up-to-date. |
| Compliance & Reporting | Generates the necessary logs and reports to help you meet regulatory requirements (like GDPR or Cyber Essentials) and demonstrate due diligence. |
Ultimately, these core functions work in concert to create a robust defensive shield, giving your business access to security capabilities that would otherwise be out of reach.
Comparing Different Security Service Models
Navigating the world of outsourced IT support can feel overwhelming. Acronyms like MSP, MSSP, and MDR are often used interchangeably, but they represent fundamentally different approaches to security.
Understanding these distinctions is the first step toward finding a partner that genuinely aligns with your organisation's risk profile, budget, and operational needs.
MSSP vs MDR vs MSP Security Offerings
Think of it as choosing the right level of medical care. A standard Managed Service Provider (MSP) is your GP, handling day-to-day IT health, keeping systems running, and resolving routine issues. A Managed Security Service Provider (MSSP) is a specialised clinic, constantly monitoring your digital vital signs for signs of trouble. Then you have Managed Detection and Response (MDR), which is the elite emergency response team, actively hunting for threats and neutralising them on sight.
The table below breaks down the key differences between these three models, helping clarify where each one fits.
| Service Model | Primary Focus | Key Activities | Best For |
|---|---|---|---|
| MSP Security | Overall IT health, system availability, and operational efficiency. | Patch management, antivirus updates, basic firewall configuration, user support. | Businesses needing foundational IT support with basic security protections in one package. |
| MSSP | 24/7 security monitoring, threat detection, and alerting. | SIEM management, log analysis, vulnerability scanning, alert triage. | Organisations needing constant network visibility and early threat warnings. |
| MDR | Proactive threat hunting and rapid incident response. | Endpoint detection and response (EDR), threat intelligence analysis, guided remediation, active threat containment. | Businesses with a high-risk profile or compliance needs that require an active, hands-on defence. |
Each model serves a distinct purpose. An MSP keeps the lights on, an MSSP watches the perimeter, and an MDR team actively patrols the grounds. Understanding this is crucial to building a security strategy that delivers the right level of protection for your business.
MSP Security: The General Practitioner
An MSP’s security offerings are typically an extension of their core IT management services. They are excellent for maintaining fundamental security hygiene—the essential basics that every business needs—but they aren't equipped for sophisticated threat detection or a full-scale incident response.
Their primary objective is to ensure operational continuity. Security is a component of that, but it is not their sole specialisation. For many small businesses, this is a sensible and adequate starting point.
MSSP: The 24/7 Monitoring Specialist
An MSSP is entirely focused on security. They deploy and manage a suite of security tools, most notably a Security Information and Event Management (SIEM) system, to deliver continuous monitoring and alerts.
The primary role of an MSSP is to provide visibility and early warnings. They are the watchtowers of your digital fortress, designed to spot trouble on the horizon and raise the alarm before it reaches the gates.
An MSSP’s team analyses security logs and alerts around the clock, cutting through the noise to pinpoint genuine threats. However, their responsibility often ends at notification. The actual remediation work of responding to and fixing the threat may still fall to your internal team or MSP.
This decision tree helps visualise the strategic choice between keeping security in-house or engaging a specialised provider.
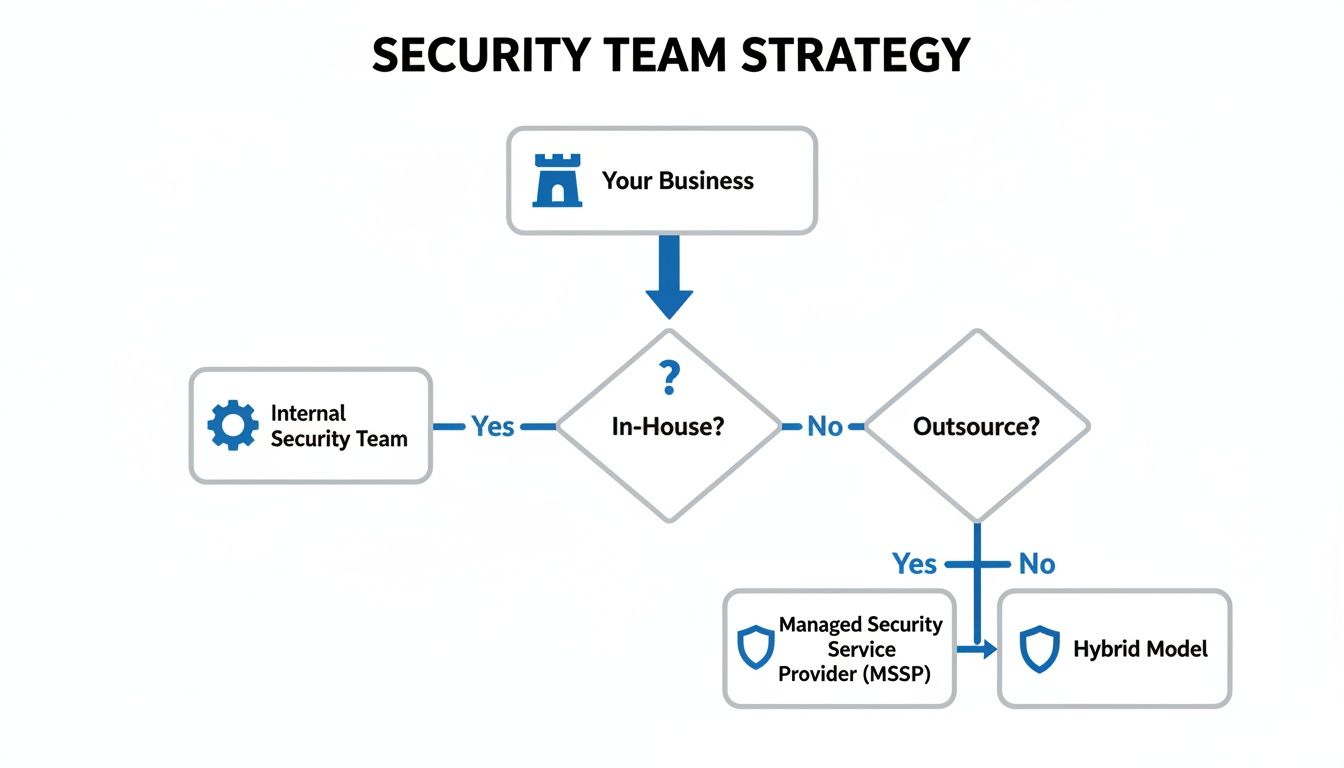
As the flowchart illustrates, the decision to outsource is often driven by a need for specialised skills and 24/7 coverage that are incredibly difficult and expensive to build from the ground up.
MDR: The Elite Threat Hunting Team
Managed Detection and Response (MDR) is the most proactive and hands-on security model. If an MSSP is the watchtower, an MDR provider is the elite response team that actively patrols the grounds, hunts for hidden intruders, and deals with them directly.
MDR services go far beyond simple alerts. They combine advanced technology with human expertise to proactively hunt for threats that may have bypassed traditional defences. When a threat is found, the MDR team doesn't just send an email—they actively intervene to contain and neutralise it. This is about taking decisive action, not just observation.
Choosing between these models isn't about which one is "best," but which one is right for your business. An MSP provides essential IT maintenance, an MSSP delivers crucial visibility, and an MDR offers an active defence. For many organisations, a successful strategy involves layering these services, relying on a partner with deep expertise to integrate them into a single, cohesive security programme.
Essential Components of Modern Managed Security
Understanding what constitutes a top-tier managed security service can feel like comparing a simple burglar alarm to a multi-layered fortress. One just makes a noise; the other actively defends. A truly protective service isn’t a single piece of software but a fusion of intelligent technologies and human expertise working in tandem to shield your business.
To make an informed choice, you need to look past marketing slogans and understand the core components that make up a serious security offering. These are the foundations of a robust defence, ensuring you receive proactive protection, not just a system that tells you when it’s already too late.
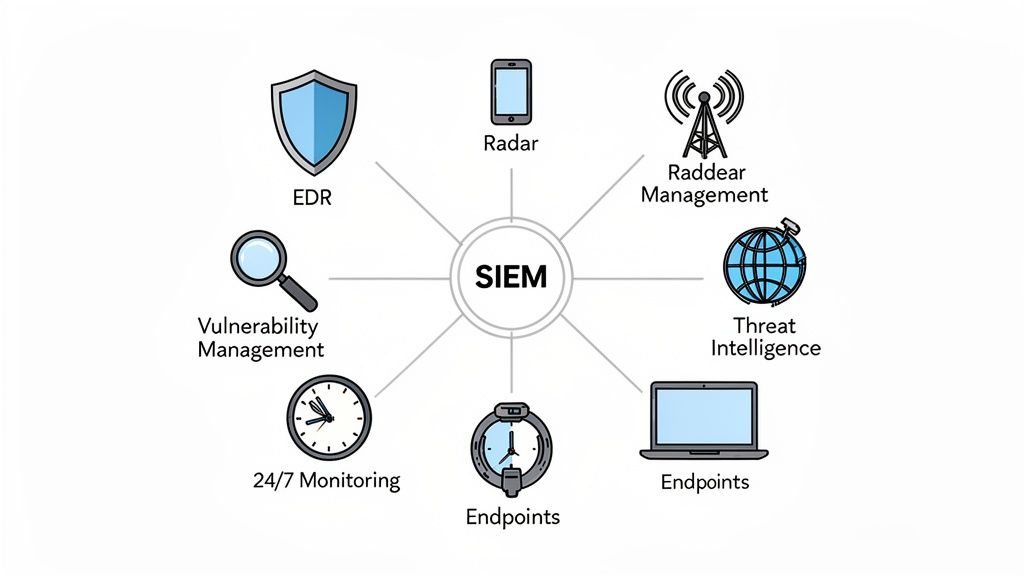
At the centre of this ecosystem is the technology that acts as the command centre, giving your security team a single, clear picture of everything happening across your network.
Security Information and Event Management (SIEM)
Think of a Security Information and Event Management (SIEM) system as the central nervous system of your entire security operation. It's a powerful platform that collects, correlates, and analyses log data from every corner of your IT environment—firewalls, servers, cloud applications, and individual endpoints.
Its primary function is to connect the dots between seemingly unrelated events to spot the subtle indicators of an attack. A single failed login is noise. A hundred failed logins from different countries in under two minutes is a clear signal of a brute-force attack, and a SIEM is designed to detect it instantly.
Effective managed security is built on robust tools like SIEM. For those exploring their options, a guide to open-source SIEM solutions can offer useful insights into how these platforms operate.
24/7 Threat Intelligence and Monitoring
Cyber threats don’t operate on a 9-to-5 schedule, which is why round-the-clock monitoring is non-negotiable. A proper managed security service provides a 24/7 Security Operations Centre (SOC), staffed by analysts who are constantly watching over your network.
This team isn't just waiting for alarms. They are actively fed a continuous stream of threat intelligence, providing critical context on emerging cybercrime trends. This includes:
- New Attack Methods: Understanding the latest tactics, techniques, and procedures (TTPs) used by cybercriminals.
- Emerging Malware: Identifying new strains of ransomware or spyware as they appear.
- Known Bad Actors: Tracking IP addresses and domains associated with active threat groups.
This intelligence transforms generic monitoring into a focused, proactive hunt for the specific threats most likely to target your business and industry.
Proactive Vulnerability Management
It is always better to fix a weakness before an attacker finds it. Vulnerability management is the ongoing process of scanning your systems, applications, and network devices to identify security gaps. This is fundamentally different from a simple annual check-up.
A strong vulnerability management programme doesn’t just find flaws; it prioritises them based on severity and the likelihood of exploitation. This allows your business to address the most dangerous issues first, systematically reducing your attack surface over time.
This proactive mindset is crucial. Instead of waiting for an attacker to discover a hole in your defences, your security partner finds and helps you patch it first. You can see how this fits into a broader strategy by learning more about regular cyber security assessments.
Advanced Endpoint Detection and Response (EDR)
Traditional antivirus software is no longer sufficient to combat modern threats. Endpoint Detection and Response (EDR) provides a much deeper, more intelligent layer of protection for your endpoints—the laptops, servers, and mobile devices that are the most common entry points for an attack.
EDR tools work by continuously monitoring all activity on these devices. When suspicious behaviour is detected—like a Word document attempting to encrypt your files—the EDR can instantly quarantine the device from the network, stopping the threat in its tracks. This rapid, automated containment is critical for preventing fast-moving attacks like ransomware from causing widespread damage.
When you bring these components together—SIEM, 24/7 monitoring, vulnerability management, and EDR—you create a truly comprehensive shield. As you evaluate IT managed security services providers, confirming these core elements are part of the package is the best way to ensure you are investing in a service that can effectively protect your business.
Enhancing Security in Microsoft 366 and Azure
For the millions of businesses operating on the Microsoft cloud, the native security tools within Microsoft 365 and Azure are incredibly powerful. But that power can be a double-edged sword; they're often complex and difficult to manage effectively. An it managed security services provider doesn’t replace these tools. Instead, they act as a force multiplier, transforming a suite of complicated features into a cohesive, fully managed security operation.
This approach is about maximising the value of your existing Microsoft investment. Rather than leaving powerful platforms underutilised, a skilled partner integrates directly into your environment, taking control of the tools you already own.
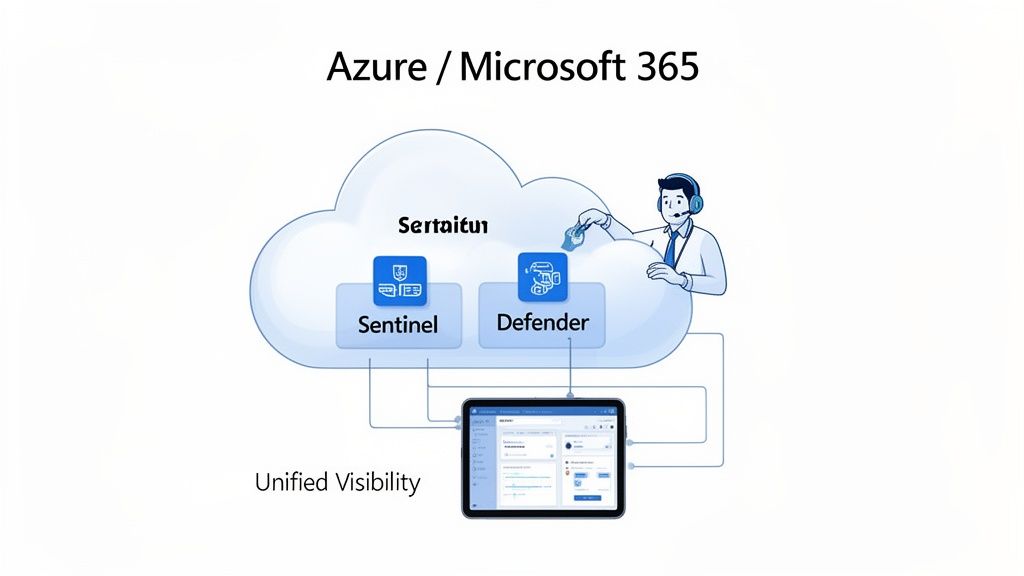
This turns potent but often dormant capabilities into an active, enterprise-grade defence, configured and managed by experts who live and breathe the Microsoft ecosystem.
Unifying Visibility With Microsoft Sentinel
Microsoft Sentinel is the central nervous system for security in a modern cloud environment. As a SIEM and SOAR (Security Orchestration, Automation, and Response) solution, it's designed to ingest security data from your entire digital estate—from Azure and Microsoft 365 to other clouds and on-premise systems.
However, its true value is unlocked only through expert configuration and continuous fine-tuning. A managed security partner takes on this heavy lifting. They will:
- Connect Data Sources: Integrate logs from Azure Active Directory, Microsoft Defender, firewalls, and third-party apps to create a single, unified view of your security posture. For more context, our guide on what Azure Active Directory is offers a deeper dive into this key component.
- Develop Custom Analytics Rules: Go beyond default templates by writing and refining rules that are laser-focused on detecting threats specific to your business and industry.
- Automate Responses: Build automated playbooks that can instantly isolate a compromised user account or block a malicious IP address, containing threats in seconds, not hours.
Without expert management, Sentinel can quickly become just another source of alert fatigue. With it, the platform becomes the intelligent, responsive core of your security operations.
Proactive Defence With Microsoft Defender
The Microsoft Defender suite is a best-in-class collection of tools for protecting everything from endpoints and identities to cloud apps and email. The primary challenge for most organisations is orchestrating these different modules to work in harmony. This is where a managed security service delivers significant value.
A managed security partner acts as the conductor for your Microsoft Defender orchestra. They ensure each instrument plays its part perfectly, turning individual security signals into a unified, proactive defence that stops attackers before they can establish a foothold.
A provider will manage the entire Defender lifecycle, from initial policy configuration to ongoing threat hunting and incident response. This involves fine-tuning Attack Surface Reduction rules, investigating alerts from Defender for Endpoint, and shutting down phishing campaigns identified by Defender for Office 365. This coordinated approach is essential for building a resilient security posture that leverages the full power of your Microsoft licences.
By entrusting the management of these platforms to a dedicated team, you ensure your Microsoft 365 and Azure environments are not just feature-rich, but genuinely secure. This strategic oversight turns powerful tools into a tangible, protective shield for your business.
How to Choose the Right Security Partner
Selecting the right provider for your IT managed security services is a critical decision that goes far beyond a simple price comparison. You aren’t just buying a service; you are entrusting a partner with the keys to your most critical digital assets. A structured approach that evaluates expertise, responsiveness, and cultural fit is essential.
The goal is to find an organisation that feels like a true extension of your own team—a trusted advisor, not just another vendor sending automated alerts. This means asking the right questions from the outset to ensure their skills and approach align with your business needs.
Verifying Technical Expertise and Industry Experience
Not all security providers are created equal. The first step is to cut through the marketing language and look for demonstrable experience. A provider who excels at protecting retail businesses may lack understanding of the strict data privacy regulations a healthcare organisation must follow.
Ask potential partners for specific, anonymised examples of how they have helped businesses similar to yours. Investigate their technical certifications and accreditations. In the UK, key credentials to look for include:
- Cyber Essentials Plus: A government-backed scheme that demonstrates strong foundational cybersecurity hygiene.
- ISO 27001: An international standard for information security management, proving adherence to strict, audited processes.
- CREST Accreditation: A strong indicator of high-quality capabilities in areas like penetration testing and incident response.
These certifications are not just badges; they are tangible proof that a provider meets recognised industry standards, providing a solid baseline of assurance.
Scrutinising SLAs and Communication Protocols
When a security incident occurs, every second counts. That's why a provider's Service Level Agreements (SLAs) for incident response are one of the most critical elements to verify. Do not accept vague promises; you need to see firm commitments.
What is their guaranteed time to respond to a critical alert? How quickly will they act to contain a threat? An SLA isn't just a contractual detail—it's a direct measure of how seriously they take your protection when an incident occurs.
Beyond response times, assess their communication style. Will you receive clear, actionable reports that explain what happened, what they did, and what you need to do next? Or will you be swamped with technical jargon and a stream of low-priority alerts? Clear, effective communication is the foundation of a successful partnership.
Assessing Cultural Fit and Strategic Alignment
While technical skills are vital, a provider's cultural fit is equally crucial for a long-term relationship. Do they take the time to understand your business goals and risk appetite? A true security partner should act as a strategic advisor, helping you make informed decisions that balance robust security with operational needs. For a deeper look into costs, our article on managed IT services pricing offers valuable context.
Bringing an MSSP on board also introduces third-party risk. This is where tools like effective third-party risk management software become important, helping you continuously monitor your vendor's compliance and security posture.
Ultimately, you are looking for a partner invested in your success. They should offer proactive guidance that helps you build a more secure and resilient organisation over time. This collaborative approach is what separates a simple service vendor from a genuine security partner.
Real-World Scenarios of Managed Security
Theory and technical specifications are one thing, but seeing IT managed security services in action is where the value becomes clear. Let's move beyond the abstract and examine two real-world (but anonymised) scenarios that demonstrate how a strong security partnership protects a business and enables its growth.
These examples illustrate how the right expertise transforms security from a necessary expense into a strategic business driver.
Preventing a Ransomware Catastrophe for a Retailer
Consider a mid-sized retail company juggling multiple locations with a small, overworked IT team. They were in a constant state of reaction, fending off daily phishing emails and malware alerts. They had standard antivirus and firewalls but knew they were one bad click away from a serious incident like ransomware.
They engaged a managed security provider. The first step was deploying an advanced Endpoint Detection and Response (EDR) solution backed by 24/7 monitoring. It didn't take long to prove its worth. A few weeks later, late on a Friday evening, the system flagged suspicious activity on a server. A malicious file, disguised as a routine system update, was attempting to execute and encrypt data.
The provider’s Security Operations Centre (SOC) team detected it instantly. They immediately isolated the server from the network, stopping the attack dead in its tracks. Instead of facing a nightmare scenario on Monday morning with a massive ransom demand, the retailer experienced zero downtime. It was business as usual. Proactive threat hunting and a rapid, expert-led response prevented a disaster that could have crippled them financially and destroyed their reputation.
For this retailer, the service was not just about software; it was about having a team of experts ready to make the right decision at a critical moment. That is the core of managed security—turning a potential catastrophe into a contained, manageable event.
Enabling Growth Through Compliance for a Professional Services Firm
A growing professional services firm was pursuing a large contract with a major corporation. The catch? To even be considered, they had to achieve a specific cybersecurity certification, proving they could handle sensitive client data securely. Their in-house team was excellent at their day jobs but lacked the niche expertise and resources to navigate the complex compliance requirements.
They partnered with a managed security provider specialising in their industry. The partner conducted a full gap analysis, implemented the necessary technical controls, and generated all required documentation. Crucially, they didn’t just get the firm through the initial audit; they provided ongoing management and evidence gathering to ensure they remained compliant.
This partnership was pivotal. The firm not only won the lucrative contract but also used their new, certified security posture as a major selling point to attract other high-value clients. In this case, managed security was not just a defensive measure—it was a direct business enabler that opened doors that would have otherwise remained shut.
Your Questions About Managed Security, Answered
Engaging a partner for your IT managed security services is a major strategic decision. It is natural to have practical questions about how it all works, from cost justification to what happens during a real threat.
We've compiled straightforward answers to the most common questions we hear from business leaders, aiming to provide clarity and help you move forward with confidence.
How Do I Justify the Cost to My Board?
This is a common challenge, but it is about framing the conversation correctly. Justifying investment in managed security is not about cost—it is about risk mitigation. Instead of presenting it as another line-item expense, position it as business insurance against a catastrophic event that could cripple your operations.
Consider this: a single ransomware attack can cost millions in downtime, recovery efforts, and regulatory fines. That figure far exceeds the predictable monthly fee of a managed service. You can also calculate the cost to build an equivalent in-house 24/7 security team, factoring in salaries, continuous training, and expensive technology licensing. When you run the numbers, a managed service almost always delivers a higher level of expertise for a fraction of the cost.
What Does the Onboarding Process Look Like?
A smooth, structured onboarding process is crucial. While every provider has a unique approach, a typical implementation follows a clear, phased process designed to minimise disruption and establish protection from day one.
- Discovery and Scoping: We begin by sitting down with you to fully understand your IT environment, specific risk profile, and any compliance requirements you need to address.
- Tool Deployment: We then carefully deploy the necessary technology—such as endpoint detection agents, log collectors, and network sensors—across your systems.
- Configuration and Tuning: This is where expertise comes into play. We configure the security platform (like a SIEM) and fine-tune the rules for your specific environment to minimise false positive alerts.
- Baseline and Go-Live: We spend a short period establishing a baseline of "normal" activity on your network. Once that's set, your 24/7 monitoring and response services officially commence.
A good partner ensures this process is seamless and transparent, keeping you informed at every stage.
What Happens During a Real Security Incident?
This is the moment your partnership proves its value. When a genuine threat is detected, a well-defined incident response plan, guided by pre-agreed Service Level Agreements (SLAs), kicks in immediately.
The entire process is built for speed and precision. The goal is to move from detection to containment in minutes, not hours, neutralising the threat before it can spread and cause widespread damage.
First, the Security Operations Centre (SOC) team instantly validates the alert to confirm it's not a false positive. Next, they take immediate containment actions, such as isolating an infected laptop from the network. Only then are you notified, with clear, actionable information about what happened, what was done, and any steps your team might need to take. This expert-led, rapid response is the core benefit of managed security.
Navigating the complexities of modern cybersecurity is not something you should do alone. For organisations seeking the structured support and strategic guidance needed to build a resilient, future-ready security posture, expert consultation can make all the difference. Book a free consultation to discuss your security needs.



